Guarding the Gates: Securing Web Applications in Python with User Authentication and Authorization
The internet thrives on interaction, and web applications are the gateways to this exchange. But with great access comes great responsibility – the responsibility to secure user data and ensure authorized actions. Python, a popular language for web development, offers robust tools to build this security layer. This article explores user authentication and authorization, the cornerstones of securing web applications in Python.
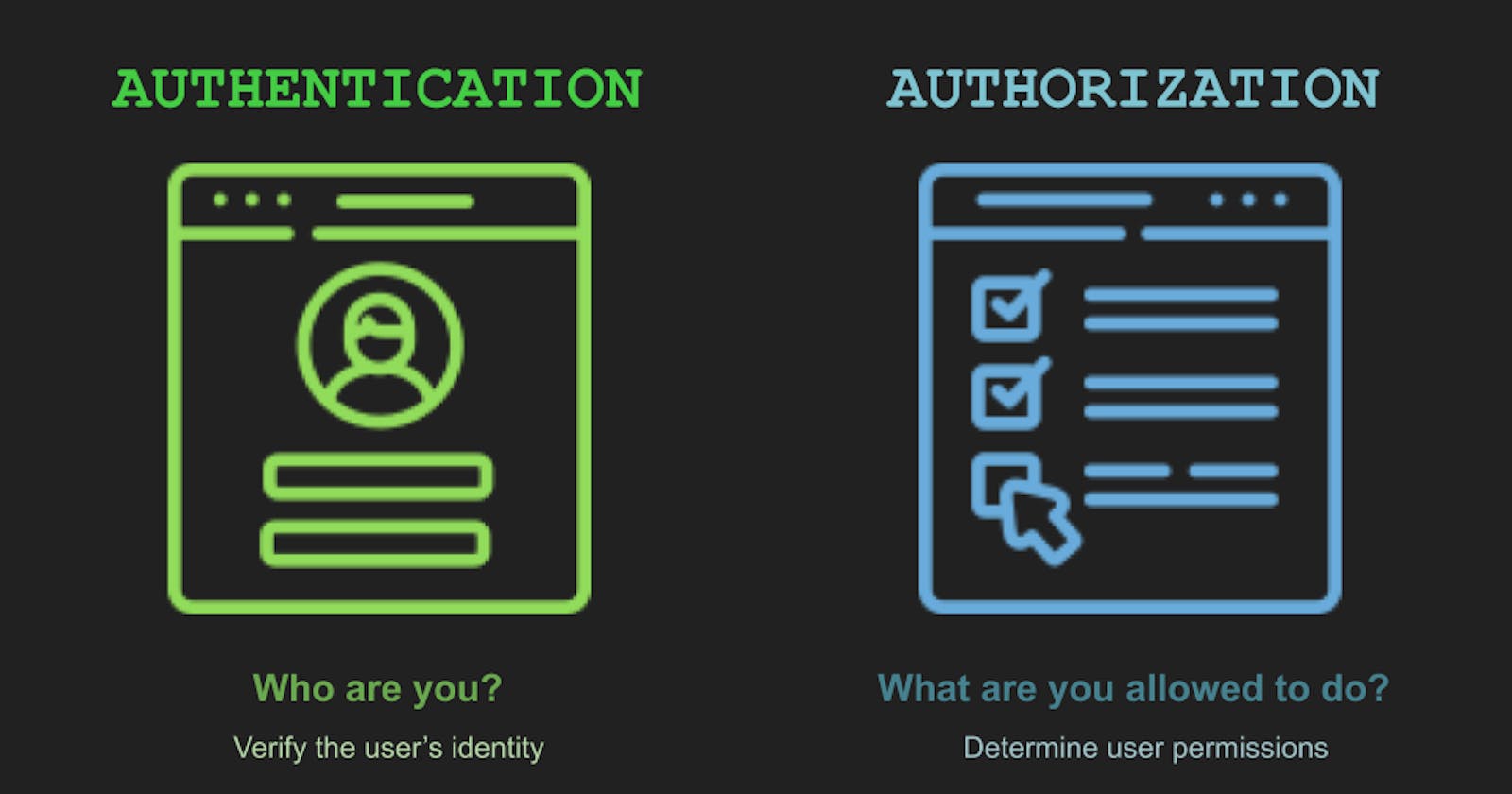
The Authentication Fortress: Verifying User Identity
Authentication is the first line of defense, ensuring only authorized users can access your application. Here are common authentication mechanisms:
Username and Password: The classic approach where users create credentials for login. Libraries like
Flask-LoginorPasslibcan simplify password hashing and storage.Social Login: Users can log in using existing social media accounts (e.g., Google, Facebook). Frameworks like Flask-Oauthlib can streamline this integration.
Token-Based Authentication: Users receive a token upon successful login, granting access for a limited duration. Libraries like
jsonwebtokencan help manage token generation and validation.
Building the Authentication Flow:
Here's a simplified example of a login process using username and password:
Login Form: Users submit their credentials through a login form.
Credential Validation: The server retrieves the user's hashed password from the database using a library like SQLAlchemy.
Hashing and Comparison: The submitted password is hashed using the same algorithm and compared to the stored hash.
Session Management: Upon successful login, a session is created to identify the user throughout their interaction with the application. Flask-Session can manage user sessions securely.
Authorization: Defining Access Levels
Once a user is authenticated, authorization comes into play. It determines what actions a user can perform based on their assigned role or permissions. Here are common approaches:
Role-Based Access Control (RBAC): Users are assigned roles (e.g., admin, editor, user) with predefined access levels. Libraries like
Flask-Securitycan simplify RBAC implementation.Attribute-Based Access Control (ABAC): Access decisions are based on user attributes, resource attributes, and the action being performed. Frameworks like Flask-Principal can facilitate ABAC.
Enforcing Authorization:
Here's a simplified example of authorization using roles:
Protected Resource: A specific route or endpoint in your application requires a certain role for access.
Role Verification: The framework checks the user's role against the required role for the resource.
Access Granted/Denied: If the user has the necessary role, access is granted. Otherwise, an error message is displayed, or the user is redirected to an unauthorized access page.
Additional Security Measures:
Secure Password Storage: Never store passwords in plain text. Use hashing algorithms like bcrypt or Argon2.
Input Validation: Sanitize user input to prevent malicious code injection attacks (XSS, SQL injection). Libraries like
Werkzeug(part of Flask) offer validation tools.Session Management: Set appropriate expiration times for sessions and implement secure session handling practices.
Regular Updates: Keep your web framework, libraries, and dependencies updated to address security vulnerabilities.
To Summarise,by implementing robust user authentication and authorization mechanisms, you build a secure foundation for your Python web applications. Remember, security is an ongoing process. Stay informed about best practices and adapt your strategies as needed. With a focus on user identity verification and access control, you can create a safe and trustworthy environment for your users.